Creating a new cybersecurity category phishing detection response pdr – Creating a new cybersecurity category, phishing detection response (PDR), is crucial in today’s digital landscape. This comprehensive guide explores the intricacies of building a robust PDR system, from defining the category itself to implementing effective strategies and measuring success. We’ll delve into various methodologies, tools, and best practices, ultimately providing a roadmap for organizations to protect themselves against evolving phishing threats.
The core of a strong PDR strategy lies in understanding the different types of phishing attacks and developing tailored responses. We’ll examine the key characteristics that distinguish PDR from other cybersecurity categories and explore the essential tools and technologies used to detect and respond to these attacks. Implementing a PDR program effectively involves integrating it seamlessly into existing security infrastructure, training personnel, and monitoring key performance indicators (KPIs).
Defining the Cybersecurity Category
Phishing detection response (PDR) is a crucial component of any robust cybersecurity strategy. It focuses specifically on the identification, analysis, and mitigation of phishing attacks, a significant threat vector in the modern digital landscape. Understanding the intricacies of PDR is essential for organizations seeking to protect themselves from financial losses, reputational damage, and data breaches.PDR encompasses a range of activities designed to quickly and effectively respond to phishing attempts.
This includes analyzing suspicious emails, websites, and other communications, identifying the tactics and techniques used by attackers, and implementing countermeasures to prevent future attacks. This proactive approach is critical for maintaining operational continuity and safeguarding sensitive information.
Phishing Detection Response (PDR) Definition
Phishing detection response (PDR) is a cybersecurity practice focused on recognizing, investigating, and mitigating phishing attacks. It goes beyond simply detecting the attack; it involves a structured response to limit the damage and prevent recurrence. Key characteristics include a rapid response to suspicious communications, analysis of the attack vector to understand attacker tactics, and implementation of preventative measures based on the analysis.
PDR also incorporates incident reporting and potentially legal action depending on the severity and impact.
Creating a new cybersecurity category, Phishing Detection Response (PDR), requires a deep dive into process performance. Understanding the nuances of process performance versus process capability, like exploring process performance vs process capability understanding the differences , is crucial for building a robust PDR. Ultimately, a strong PDR hinges on optimizing these processes to ensure accurate and timely detection of phishing attempts.
Key Characteristics of PDR
PDR differs from other cybersecurity categories in its specific focus on phishing. While intrusion detection systems (IDS) monitor network traffic for malicious activity, PDR zeroes in on the social engineering tactics employed in phishing attacks. Malware analysis, on the other hand, focuses on the malicious code itself, while PDR concentrates on the human element and the deception used to trick victims.
Types of Phishing Attacks and PDR
Various types of phishing attacks exist, each targeting different vulnerabilities. These include spear phishing (targeted attacks), whaling (attacks against high-profile individuals), and vishing (voice phishing). PDR methodologies must adapt to the specifics of each attack type, understanding the unique characteristics of each to effectively mitigate them. For example, a spear phishing attack requires more granular analysis of the targeted individual and their organizational context, compared to a mass-distributed phishing campaign.
PDR vs. Other Cybersecurity Categories
| Category | Description | Key Features |
|---|---|---|
| PDR | Structured response to phishing attacks, encompassing detection, analysis, and mitigation. | Focuses on social engineering tactics, rapid response, and preventative measures. |
| Intrusion Detection | Monitoring network traffic for malicious activity and anomalies. | Identifies unauthorized access attempts and security breaches. |
| Malware Analysis | Examining malicious software to understand its functionality and behavior. | Focuses on the technical aspects of malware, identifying its capabilities and potential damage. |
PDR Methodology
Phishing Detection Response (PDR) is a crucial aspect of any comprehensive cybersecurity strategy. A well-defined PDR methodology ensures swift and effective handling of phishing attacks, minimizing potential damage and maximizing the recovery process. This approach involves a structured process, utilizing various detection methods, and culminating in a robust response strategy.Modern phishing attacks are sophisticated and constantly evolving. Therefore, a dynamic and adaptable PDR methodology is essential.
This methodology not only identifies phishing attempts but also helps organizations understand the root causes of successful attacks, enabling proactive measures to strengthen their defenses.
Different Methodologies Used in Modern Phishing Detection
Modern phishing detection relies on a combination of techniques. These methodologies include, but are not limited to, email filtering, user training, and advanced threat detection systems. Email filtering solutions analyze incoming emails for suspicious content, such as malicious links or attachments. User training programs educate employees about recognizing phishing attempts, which is a vital line of defense. Advanced threat detection systems often utilize machine learning and AI to identify sophisticated phishing attempts that traditional methods might miss.
Stages Involved in a Complete PDR Process, Creating a new cybersecurity category phishing detection response pdr
A robust PDR process encompasses several stages. These stages, when followed methodically, can significantly reduce the impact of a phishing attack. They typically include the initial detection, triage, containment, eradication, recovery, and post-incident analysis. These steps ensure that the incident is handled effectively and efficiently, minimizing disruption to operations and preventing future attacks.
Structured Approach for Building a Robust PDR Strategy
Building a robust PDR strategy requires a structured approach. A key element is establishing clear roles and responsibilities for handling phishing incidents. Defining communication protocols is crucial for swift and effective responses. Having a documented incident response plan that details the steps involved in each stage of the PDR process is also vital.
- Clear Roles and Responsibilities: Designating specific individuals or teams for different tasks (e.g., incident reporting, technical analysis, communication) is essential. This ensures accountability and minimizes confusion during an incident.
- Communication Protocols: Establishing clear communication channels (e.g., email, instant messaging, dedicated phone lines) for rapid and accurate information sharing is critical. This helps to keep stakeholders informed and coordinated.
- Documented Incident Response Plan: Creating a detailed plan that Artikels the procedures for each stage of the PDR process (detection, containment, eradication, recovery, and post-incident analysis) is crucial. This plan should be regularly reviewed and updated to reflect evolving threats and best practices.
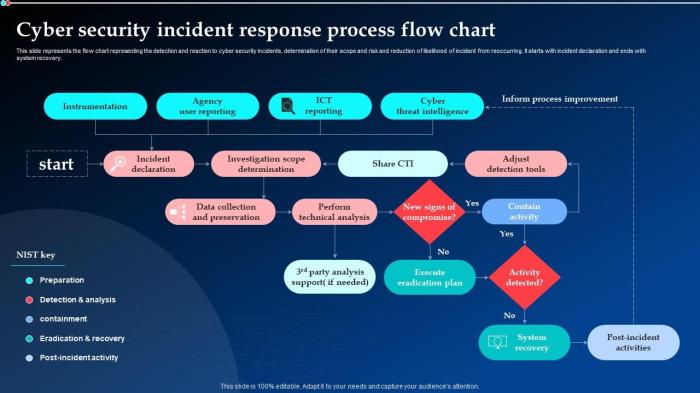
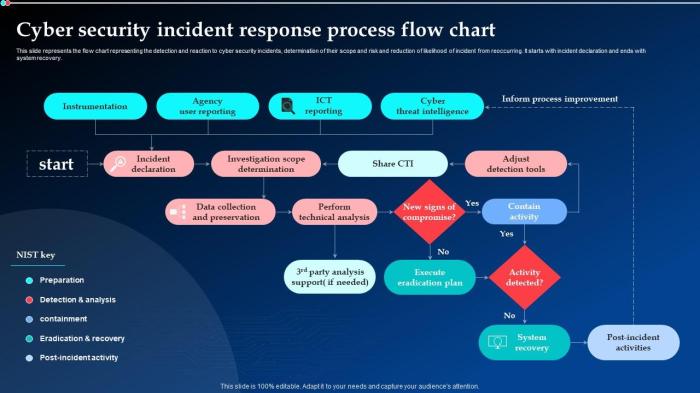
Flow Chart Illustrating the Phishing Response Process
A flow chart can visually represent the steps involved in a phishing response process. This visualization aids in understanding the sequential nature of actions and facilitates a smooth and efficient response.“`+—————–+| Phishing Alert |+—————–+| Detected |—>+—————–+| Initial Triage |—>+—————–+| Assessment |—>+—————–+| Containment |—>+—————–+| Eradication |—>+—————–+| Recovery |—>+—————–+| Post-Incident |—>| Analysis |—>+—————–+| Documentation |—>+—————–+| Lessons Learned |—>+—————–+| Reporting |—>+—————–+“`This flow chart shows a streamlined approach, emphasizing the crucial stages from initial detection to final reporting and learning.
Each step, while seemingly distinct, is interconnected and vital for a successful phishing response.
PDR Tools and Technologies: Creating A New Cybersecurity Category Phishing Detection Response Pdr
Phishing detection and response (PDR) relies heavily on a suite of tools and technologies. These tools automate many tasks, allowing security teams to react quickly and effectively to phishing threats. Their effectiveness hinges on the sophistication of the threat landscape and the proactive nature of the security strategy.Effective PDR requires a multi-layered approach, leveraging various tools and technologies to detect and respond to phishing attacks at different stages.
This encompasses everything from email filtering to advanced threat intelligence analysis. Understanding the strengths and weaknesses of each tool is crucial for building a robust defense against phishing.
Email Filtering and Security Gateways
Email filtering systems are the first line of defense against phishing attacks. They employ various techniques to identify and block malicious emails, often relying on predefined signatures, blacklists, and machine learning algorithms. Security gateways, acting as the entry point for network traffic, also play a significant role in filtering phishing attempts. These systems can identify malicious links and attachments before they reach users’ inboxes.
Endpoint Detection and Response (EDR) Tools
EDR solutions provide a comprehensive view of activities on endpoints, such as laptops and desktops. They can detect suspicious behavior, such as unusual file access or network connections, that might indicate a phishing attack. These tools often integrate with other security systems to provide a holistic view of the threat landscape. EDR solutions can automatically quarantine infected systems and prevent further damage.
Security Information and Event Management (SIEM) Systems
SIEM systems collect and analyze security logs from various sources, including email servers, firewalls, and endpoints. This data can reveal patterns and anomalies indicative of phishing campaigns. By correlating events, SIEM systems can provide valuable insights into the scope and impact of an attack. These systems also aid in threat hunting, enabling security analysts to proactively identify and investigate potential threats.
Phishing Simulation and Awareness Training Platforms
Phishing simulations allow organizations to test the effectiveness of their security awareness training programs. These platforms send simulated phishing emails to employees, allowing them to identify and report suspicious messages. This proactive approach helps users develop better judgment and critical thinking skills, which are crucial in recognizing actual phishing attempts. Feedback from these simulations can also inform the development of more effective security training materials.
Threat Intelligence Platforms
Threat intelligence platforms provide up-to-date information on current phishing campaigns, tactics, and techniques. These platforms often incorporate open-source intelligence (OSINT) and other sources to identify emerging threats. This real-time information can be invaluable in adapting security measures to the ever-evolving threat landscape. Using threat intelligence, security teams can proactively block phishing attempts and mitigate potential damage.
Comparison of PDR Tools
| Tool | Pros | Cons |
|---|---|---|
| Email Filtering Systems | Cost-effective, readily available, initial line of defense | Can be easily bypassed by sophisticated attacks, limited ability to detect zero-day threats |
| EDR Tools | Comprehensive endpoint protection, real-time threat detection, detailed activity logs | Can be complex to implement and manage, high cost of implementation and maintenance, potentially high false positive rate |
| SIEM Systems | Centralized security log management, advanced threat correlation, threat hunting capabilities | Complex to implement and manage, high cost of implementation, requires skilled personnel for effective use |
| Phishing Simulation Platforms | Effective in improving user awareness, data-driven approach to training, cost-effective in the long run | Requires ongoing maintenance, effectiveness relies on user engagement |
| Threat Intelligence Platforms | Proactive threat identification, real-time information, adaptation to emerging threats | Requires subscription fees, reliance on external sources can pose some risk, information overload |
PDR Implementation Strategies

Implementing a robust Phishing Detection Response (PDR) program is crucial for any organization’s cybersecurity posture. This involves more than just installing software; it requires a structured approach that integrates PDR into existing security processes and cultivates a security-conscious culture. Successful implementation hinges on careful planning, adequate resources, and continuous improvement.Effective PDR implementation is not a one-time event; it’s a continuous process requiring ongoing evaluation and adaptation.
This iterative approach ensures that the PDR program remains relevant and effective in countering evolving phishing threats. Successful integration into existing security infrastructure is key to ensuring that the PDR program seamlessly complements existing security measures, rather than creating redundancy or conflict.
Integrating PDR into Existing Security Infrastructure
The successful integration of PDR into an existing security infrastructure relies on a thoughtful approach. It’s not simply about adding another layer, but rather about enhancing existing security protocols. This involves aligning PDR procedures with incident response protocols and existing security information and event management (SIEM) systems. Data from the PDR system can be integrated with SIEM data to provide a more comprehensive view of potential threats and malicious activities.
A clear communication plan between the security team and other departments is also critical for timely and effective incident response.
Necessary Resources and Personnel
Implementing a PDR program requires dedicated resources, including personnel with specialized skills and knowledge. This may include dedicated PDR analysts, security awareness trainers, and incident responders. The size of the team will depend on the organization’s size, complexity, and the volume of phishing attempts encountered. It’s also essential to consider budget allocations for software licenses, training materials, and potential legal counsel related to incidents.
A dedicated budget for ongoing maintenance and upgrades to PDR tools is also important.
Creating a new cybersecurity category, Phishing Detection Response (PDR), requires careful thought. It’s not just about the technical aspects; effective PDR also needs a strong brand identity, which ties in closely with the overall marketing strategy. Understanding how branding and marketing work together, like in branding vs marketing how do they work together , is crucial for building a recognizable and trustworthy system for detecting and responding to phishing attempts.
Ultimately, a solid brand and a well-defined marketing plan will contribute to a successful PDR system.
Training and Awareness Programs
Effective PDR hinges on employee awareness and training. Regular training programs focused on phishing awareness are essential for equipping employees to identify and report suspicious emails. This includes simulations and practical exercises, and a variety of training methods can be employed. This might include interactive modules, videos, quizzes, or phishing simulations. A clear communication strategy about the importance of reporting suspicious emails, coupled with a robust reporting system, is critical.
A regular review and update of training materials is essential to keep pace with evolving phishing tactics.
Methods for Improving Employee Awareness
Regular phishing simulations are an effective method to assess employee susceptibility to phishing attacks and reinforce training. Interactive training modules and videos can reinforce key concepts and provide real-world examples. A dedicated communication channel for security alerts and reminders, accessible across various platforms, can reinforce awareness. Security awareness campaigns can be integrated into broader company communication channels.
The use of gamification elements within training programs can increase engagement and motivation, making learning more interactive and enjoyable. Encouraging employees to share their knowledge and experiences with colleagues can also strengthen awareness and collaboration.
PDR Metrics and Evaluation
Measuring the effectiveness of a Phishing Detection Response (PDR) system is crucial for demonstrating its value and identifying areas for improvement. A robust evaluation framework provides insights into the system’s performance, allowing organizations to optimize their security posture and proactively mitigate future threats. This involves not just detecting phishing attempts but also understanding the speed and impact of the response.Effective PDR systems need to be evaluated not only on their ability to detect phishing attacks, but also on their impact on overall security posture.
Metrics should encompass the entire incident response process, from initial detection to containment and remediation. A well-defined set of KPIs will provide a clear picture of the system’s effectiveness.
Key Performance Indicators (KPIs) for PDR
Defining appropriate KPIs is vital for quantifying the success of PDR initiatives. These metrics should be aligned with organizational objectives and measurable, allowing for consistent tracking and analysis. The KPIs should cover various aspects of the PDR process, from initial detection to the overall impact on security posture.
Creating a new cybersecurity category, Phishing Detection Response (PDR), is crucial for businesses navigating the digital landscape. This involves developing robust systems to identify and respond to phishing attacks, a critical aspect of securing your organization. Implementing such a system is key to unlocking business success with digital transformation unlock business success with digital transformation , ultimately improving efficiency and protecting sensitive data.
Ultimately, a strong PDR strategy is essential for maintaining a secure digital environment in today’s interconnected world.
Phishing Detection Rate
The Phishing Detection Rate (PDR) quantifies the percentage of phishing attempts successfully identified by the system. A high detection rate indicates the effectiveness of the system in identifying malicious emails. This metric is critical for evaluating the system’s ability to identify threats before they cause harm. Methods for calculating PDR include comparing the number of phishing attempts detected to the total number of phishing attempts observed over a specified time period.
Impact on Overall Security Posture
Measuring the impact of PDR initiatives on the overall security posture involves evaluating the reduction in potential losses resulting from successful phishing attacks. This includes financial losses, reputational damage, and operational disruptions. Organizations can use metrics like the number of compromised accounts, financial losses avoided, and the time saved in response to mitigate incidents. For example, a PDR system that successfully blocks 95% of phishing attempts may prevent significant financial losses and reputational damage.
Tracking and Analyzing Phishing Detection Rates
Tracking and analyzing phishing detection rates requires meticulous data collection and analysis. This involves establishing clear criteria for identifying phishing attempts and recording the results in a central repository. Data analysis tools can provide insights into trends, patterns, and areas for improvement. For instance, analysis of detection rates across different user groups can reveal potential vulnerabilities.
Time Taken to Respond to Phishing Attacks
Measuring the time taken to respond to phishing attacks is crucial for evaluating the efficiency of the PDR system. This includes the time taken to detect the attack, investigate the nature of the threat, and implement appropriate countermeasures. Organizations can use incident response dashboards to track response times. Minimizing response time is critical to mitigating the impact of successful phishing attacks.
PDR Effectiveness Measurement Table
| KPI | Description | Measurement Method |
|---|---|---|
| Phishing Detection Rate | Percentage of phishing attempts successfully detected by the system. | Divide the number of detected phishing attempts by the total number of observed phishing attempts and multiply by 100. |
| Time to Detect | Average time taken to detect a phishing attempt after it is sent. | Record the time difference between the phishing email’s arrival and the system’s detection. Calculate the average. |
| Time to Respond | Average time taken to implement countermeasures after detection. | Measure the time from detection to remediation (e.g., blocking the sender, notifying affected users). Calculate the average. |
| Number of Compromised Accounts Avoided | Number of user accounts protected from compromise due to the PDR system. | Track instances where a phishing attempt was blocked and the user account was not compromised. |
| Financial Losses Avoided | Estimated financial losses prevented due to the PDR system’s effectiveness. | Estimate potential losses based on historical data and industry benchmarks. Subtract the losses that were prevented by the PDR system. |
PDR Best Practices and Case Studies
Phishing detection response (PDR) strategies are crucial for mitigating the escalating threat of phishing attacks. Effective PDR goes beyond simply identifying a phishing attempt; it involves a structured response that minimizes damage, learns from the incident, and strengthens defenses. This section explores best practices for designing and implementing robust PDR strategies, drawing on real-world case studies and lessons learned from past incidents.Implementing a well-defined PDR strategy is paramount to minimizing the impact of phishing attacks.
A comprehensive approach involves proactive measures to enhance awareness, establish clear incident response protocols, and ensure timely and effective containment.
Best Practices for Designing and Implementing PDR Strategies
A strong PDR strategy necessitates a proactive approach that extends beyond reactive measures. Key components include a robust awareness training program for employees, clear communication channels for reporting suspicious emails, and established procedures for isolating affected systems. Furthermore, regular assessments of the effectiveness of the PDR strategy are critical for continuous improvement.
- Employee Awareness Training: Regular phishing simulations are essential to build user awareness and identify vulnerabilities in employee behavior. Training should cover recognizing phishing tactics, such as spoofed emails, suspicious links, and malicious attachments. Practical exercises, like analyzing simulated phishing attempts, are particularly effective in reinforcing learning.
- Clear Communication Channels: Establishing a dedicated communication channel for reporting suspicious emails ensures that incidents are promptly addressed. A dedicated email address, an internal reporting portal, or a dedicated phone line for security concerns are valuable tools in facilitating the reporting process. This allows for faster response times and a coordinated approach to handling reported threats.
- Incident Response Protocols: Developing comprehensive incident response protocols is crucial for effectively managing phishing incidents. These protocols should Artikel the steps for identifying, containing, eradicating, recovering, and learning from each incident. Clear roles and responsibilities for different team members during an incident are also critical.
- System Isolation Procedures: Rapid isolation of compromised systems is essential to prevent the spread of malware. Establishing clear procedures for isolating affected systems minimizes the scope of the incident and limits the potential damage.
- Regular Assessments: Periodic assessments of the PDR strategy are critical to identify weaknesses and areas for improvement. These assessments should evaluate the effectiveness of awareness training, the efficiency of incident response procedures, and the performance of implemented technologies. The results of these assessments provide a roadmap for continuous improvement.
Real-World Case Studies and Lessons Learned
Analyzing past phishing incidents provides valuable insights into the effectiveness of different PDR strategies. The following case studies highlight successful implementations and the lessons learned from incidents that have been successfully contained.
- Case Study 1: A large financial institution successfully contained a sophisticated phishing campaign targeting high-level executives. Their robust PDR strategy, including extensive employee training, a dedicated incident response team, and advanced email filtering technologies, enabled them to identify and neutralize the threat quickly. This resulted in minimal financial loss and damage to reputation.
- Case Study 2: A mid-sized healthcare organization experienced a phishing attack that resulted in the compromise of sensitive patient data. Their initial response was slow and lacked a clear incident response plan. This incident underscored the importance of having a well-defined PDR strategy, including procedures for data breach notification and incident containment.
“A well-defined incident response plan, practiced regularly, is critical for containing the damage of a phishing attack.”
“Employee awareness training is a critical element of a robust PDR strategy. Regular simulations and interactive exercises are essential to reinforce knowledge and skills.”
“Effective communication channels for reporting suspicious activities are vital for a rapid and coordinated response to phishing attacks.”
Ultimate Conclusion
In conclusion, creating a dedicated phishing detection response (PDR) category within your cybersecurity framework is not just a best practice, it’s a necessity. By understanding the methodologies, tools, and implementation strategies Artikeld in this guide, organizations can proactively defend against phishing attacks, minimize their impact, and ultimately strengthen their overall security posture. The key is to adapt and evolve your PDR program to keep pace with the ever-changing threat landscape.
Consistent training and adaptation will ensure your PDR program remains effective.