How to disable directory browsing in WordPress is crucial for website security. Directory browsing, a common vulnerability, allows unauthorized access to files and folders on your server. This can expose sensitive information and potentially compromise your site. Understanding how to identify and prevent this risk is essential for maintaining a secure WordPress presence.
This guide will walk you through the process of identifying directory browsing vulnerabilities on your WordPress site, exploring various methods to disable it, from simple .htaccess modifications to more complex server-side configurations. We’ll also cover troubleshooting common issues and implementing robust security practices.
Introduction to Directory Browsing in WordPress
Directory browsing in WordPress, when enabled, allows users to view the contents of a website’s file system. This isn’t intended functionality; it’s a security vulnerability. Think of it like a window into the inner workings of your website, revealing files and folders that shouldn’t be publicly accessible.This seemingly innocuous feature can expose sensitive information, potentially leading to malicious activities.
Understanding how it works and why it’s a risk is crucial for securing your WordPress site. The consequences can range from minor annoyances to serious breaches.
What is Directory Browsing?
Directory browsing is a feature, often unintentionally enabled, that displays the contents of a website’s directory structure in a browser. This includes a list of files and folders, allowing users to view them without needing specific file access links. Imagine a folder structure on your computer, but accessible through a web browser. This exposure can include sensitive configuration files, backups, or even source code.
How Directory Browsing Works
WordPress, by default, does not display directory listings. However, if a server misconfigures directory access permissions, or if a plugin or theme introduces a vulnerability, the directory structure becomes visible. This happens when the server responds to a request for a directory by presenting the directory contents, rather than redirecting or handling the request in a secure way.
This can occur if the server’s web server configuration doesn’t properly handle directory requests. The result is a list of files and folders presented directly to the user.
Why is Directory Browsing a Security Risk?
Directory browsing poses a significant security risk because it exposes sensitive information to unauthorized individuals. This information can be exploited in various ways. This vulnerability allows attackers to:
- Gain access to sensitive files like database credentials, API keys, or configuration files.
- Locate and download sensitive data, including backups, source code, and other proprietary information.
- Identify potential vulnerabilities in the website’s code or infrastructure.
- Disrupt or compromise the website’s functionality.
Common Exploitation Scenarios
Directory browsing vulnerabilities are often exploited by automated scripts or malicious actors looking for weaknesses. These exploits can be triggered by:
- Incorrect file permissions: If a file or folder isn’t properly secured with appropriate permissions, an attacker can gain access.
- Vulnerable plugins or themes: Outdated or poorly coded plugins or themes can introduce security holes, allowing directory browsing.
- Misconfigured web server settings: A server misconfiguration can allow directory browsing by default. Incorrect setup can expose the entire file structure.
- Automated attacks: Automated tools can scan websites for directory browsing vulnerabilities and exploit them.
Consequences of Allowing Directory Browsing
The consequences of allowing directory browsing can vary depending on the sensitivity of the exposed information. However, the potential consequences can be severe:
- Data breaches: Exposure of sensitive data, like database credentials or API keys, can lead to a complete data breach.
- Website compromise: Attackers can use the exposed files to gain unauthorized access to the website’s server.
- Financial losses: If sensitive financial data is exposed, this can result in significant financial losses.
- Reputational damage: A security breach can damage a website’s reputation, causing users to lose trust.
Preventing Directory Browsing
Implementing proper security measures, like using strong passwords, enabling two-factor authentication, and keeping software up-to-date, can greatly reduce the risk of directory browsing.
Identifying the Problem
Detecting directory browsing vulnerabilities is crucial for securing a WordPress site. A compromised site with enabled directory browsing exposes sensitive files and directories, potentially revealing usernames, passwords, database credentials, or other confidential information. This vulnerability can lead to unauthorized access, data breaches, and severe security implications. Identifying the problem is the first step towards mitigation.Understanding the potential implications of directory browsing is vital.
It allows proactive measures to be taken, preventing attackers from exploiting this weakness. Recognizing the signs of a directory browsing vulnerability is paramount for immediate remediation.
Methods for Detecting Directory Browsing
Identifying if directory browsing is enabled involves several techniques. Directly visiting a directory in the browser is one method. If the site displays a listing of files and folders, directory browsing is likely enabled. Inspecting the website’s source code can also reveal clues. Look for HTML elements that display file names, paths, or directory structures.
Identifying Potentially Sensitive Files and Directories
A critical aspect of identifying potential security risks is scrutinizing the directory structure. Directories containing sensitive files like configuration files (.htaccess, wp-config.php), database credentials, or user data should be carefully examined. Checking for the presence of unexpected or unnecessary files or folders is a crucial step. For example, a file named “passwords.txt” or a folder labeled “private_data” should raise suspicion.
Knowing the typical directory structure of a WordPress installation helps in pinpointing unusual entries.
Analyzing Server Logs for Clues
Server logs are invaluable for uncovering directory browsing attempts. Analyzing access logs can reveal unusual requests to specific directories. Look for high numbers of requests for files or folders not typically accessed by legitimate users. For instance, frequent requests to sensitive files or directories not frequently accessed might indicate malicious activity. Correlating these requests with timestamps can help in determining the frequency and duration of the issue.
Using Command-Line Tools for File Listing Inspection
Command-line tools provide a powerful method for inspecting file listings. Tools like `ls -l` (on Linux/macOS) or equivalent commands on other systems can display detailed file information, including permissions and modification times. By analyzing file listings, patterns indicative of malicious activity can be identified. This allows for a deeper understanding of the affected directories and the nature of the potential security breach.
Want to secure your WordPress site? Disabling directory browsing is a simple but crucial step. This helps prevent unwanted access to sensitive files and folders. Understanding how to do this is important for a strong online presence, and can help you focus on more advanced strategies like cross device remarketing with Google Analytics. This powerful technique, cross device remarketing google analytics , can really boost your marketing efforts by tracking user behavior across different devices.
Ultimately, securing your site by disabling directory browsing is key to keeping your WordPress site safe and effective.
This analysis helps in understanding the extent of the compromise and potential access points.
Methods to Disable Directory Browsing
Directory browsing, a vulnerability in web servers, allows users to view the contents of a website’s file system. This can expose sensitive information, including configuration files and potentially even access to other files, making it a serious security risk for WordPress sites. Disabling directory browsing is crucial for maintaining website security and protecting against unauthorized access.Effective directory browsing prevention involves a multi-faceted approach.
Different methods cater to various levels of technical expertise and server environments. This section Artikels recommended strategies, from simple WordPress configuration adjustments to more complex server-level interventions.
WordPress Core Settings
This method is the simplest and often sufficient for basic security.
- WordPress itself offers a rudimentary level of directory browsing protection. However, this method is often not enough to completely prevent directory browsing vulnerabilities. You can adjust the file permissions within the WordPress settings.
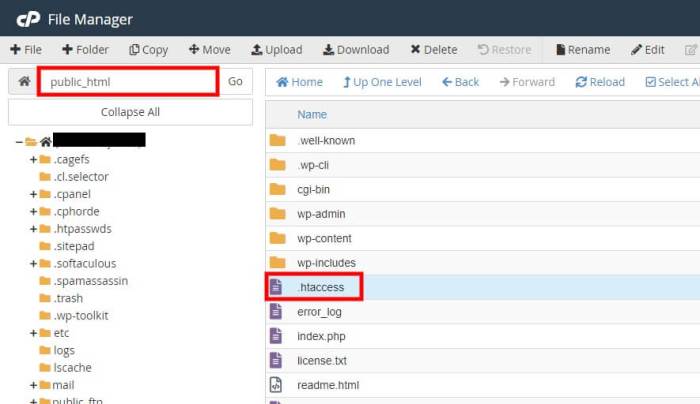
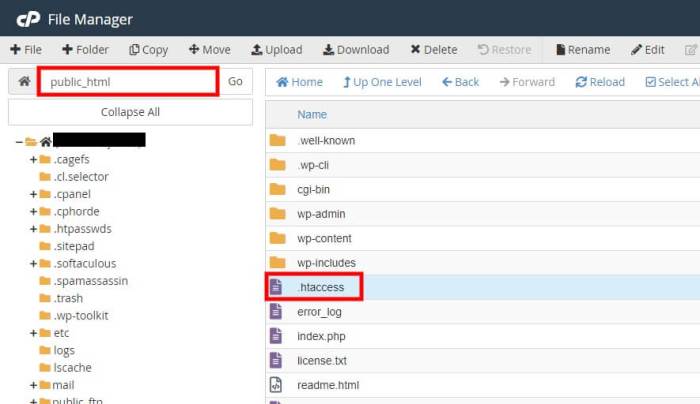
.htaccess File Modification
The .htaccess file, located in the root directory of your WordPress installation, provides a powerful tool for controlling server behavior.
- Using directives within the .htaccess file is a common method for disabling directory browsing. A crucial directive is
Options -Indexes. Adding this directive prevents the web server from displaying directory listings. This is a widely used and effective technique. For example:Options -IndexesThis directive should be placed within the .htaccess file. - Another approach is to use the
RewriteRuledirective to redirect requests for directories to a specific file, preventing directory listings. This is a more complex technique, but offers more control over the response to directory requests.
Server Configuration (Apache)
This method provides the most comprehensive control over directory browsing prevention. It requires knowledge of server configuration.
- For Apache servers, the
Options -Indexesdirective can be added to theDirectorysection in the server’s configuration file (typicallyhttpd.confor a virtual host configuration). This method directly controls the behavior of the Apache web server, providing maximum security. For example, within the Apache configuration file, ensure a line like this exists:Options -Indexes - Using the
AllowOverridedirective with the.htaccessfile is important to enable .htaccess to modify server behavior. Without this, directives in .htaccess are ignored. TheAllowOverridedirective should be included in the Apache configuration file, enabling .htaccess’s control. For example:AllowOverride All
Comparison of Methods
- WordPress core settings offer the simplest approach, but provide limited control. This is often sufficient for basic protection, but more robust methods are recommended for enhanced security.
- `.htaccess` files provide a balance between simplicity and control. It’s a good choice for most users who have some familiarity with server configuration.
- Server configuration allows the most control and customization. This is ideal for advanced users who want complete control over the web server’s behavior, but it requires a deeper understanding of server configuration.
Implementing the Chosen Method
Disabling directory browsing is a crucial security measure for WordPress websites. By preventing direct access to directories, you significantly reduce the risk of malicious actors exploiting vulnerabilities and potentially gaining unauthorized access to sensitive files or data. Implementing the chosen method, whether it’s modifying .htaccess or server configuration files, is a critical step in enhancing your site’s overall security posture.This section details the practical steps involved in disabling directory browsing using the .htaccess file and server configuration.
It also provides a comparison of the different approaches across various server types, allowing you to select the most appropriate method for your specific setup.
Disabling Directory Browsing with .htaccess
The .htaccess file, a configuration file used by Apache web servers, allows you to control various aspects of how your website functions. It’s a powerful tool for fine-tuning your site’s behavior without needing to modify the main server configuration.
- Locate your .htaccess file. This file is typically located in the root directory of your WordPress installation.
- Open the .htaccess file in a text editor. Be extremely careful when editing this file. Incorrect changes can break your website. Ensure you have a backup of your .htaccess file before making any edits.
- Add the following code to the .htaccess file. This code will prevent directory listings.
Options -Indexes
- Save the .htaccess file.
- Clear your browser cache and refresh the page to see the changes take effect.
Disabling Directory Browsing in Server Configuration
Server configuration files, such as those used by Apache or Nginx, provide more granular control over access to your website’s directories. This approach often offers more extensive security features compared to using .htaccess alone.
- Identify the server configuration file. The specific location and filename vary based on your hosting provider and server type.
- Open the server configuration file in a text editor. Again, ensure you have a backup of the file before making any modifications.
- Add the appropriate directives to block directory listings. The specific syntax depends on your server’s type, such as Apache or Nginx.
- Save the server configuration file.
- Restart the web server. This step is crucial for applying changes to the server configuration. Contact your hosting provider for the exact commands if you are unsure.
- Refresh the page to verify that the changes have been implemented.
Comparison of Directory Browsing Disablement Across Server Configurations
The table below summarizes the different syntaxes for disabling directory browsing in various server configurations. Understanding these differences allows you to choose the most appropriate method for your specific setup.
Troubleshooting Common Issues: How To Disable Directory Browsing In WordPress
Disabling directory browsing in WordPress can sometimes run into unexpected snags. This section dives into common problems you might encounter and provides solutions to help you navigate these hurdles. From plugin conflicts to server-side configuration issues, we’ll cover the most frequent challenges and offer practical steps to resolve them.
Troubleshooting WordPress directory browsing issues often involves a methodical approach. Identifying the source of the problem is key. This may require investigating plugin interactions, reviewing server permissions, or even checking the server’s configuration. By understanding the potential causes and their solutions, you can efficiently diagnose and resolve problems related to directory browsing.
Plugin and Theme Conflicts
WordPress relies on a complex interplay of plugins and themes. A poorly coded plugin or a theme with conflicting directives can sometimes disrupt the functionality of directory browsing disablers.
Want to keep prying eyes away from your WordPress site’s hidden directories? Disabling directory browsing is a crucial security step. It’s a simple process, but knowing how to use a robots.txt file can enhance your site’s security even further. Learning about website 101 how to use robot txt files will show you how to effectively control what search engines and other bots can see, making your site more robust.
Ultimately, both techniques, when combined, create a much stronger and more secure website.
- Incompatible plugins can interfere with the directory browsing disabling process. Examine plugins that were recently installed or updated. Disable suspected plugins temporarily to see if the problem persists. If disabling a specific plugin resolves the issue, it’s a strong indicator of a conflict.
- Themes can also cause issues. Ensure your active theme is compatible with the directory browsing disabler. Check for theme updates and consider switching to a different theme to determine if the theme is the root cause. Sometimes, a theme’s custom functions can conflict with the disabler.
Permission Issues
WordPress relies on file and directory permissions for proper functionality. Incorrect permissions can prevent the directory browsing disabler from functioning correctly.
- Incorrect directory permissions can hinder the disabler’s ability to block directory access. Verify that the web server user (often ‘www-data’ or similar) has the necessary permissions to read, write, and execute files and directories. Use the file system permissions of the server to ensure the correct permissions are applied to the necessary files and directories. Adjust permissions as needed.
- Specific files or directories might have incorrect ownership or permissions. Use the operating system’s file management tools to check and adjust the ownership and permissions of the affected files or directories. This might involve changing the owner of the files to the web server user and adjusting the read/write/execute permissions for the web server user.
Server-Side Configuration Problems
Server-side misconfigurations can also lead to directory browsing issues. Understanding your server’s setup is crucial for resolving these issues.
- Incorrect server configuration, such as a misconfigured Apache or Nginx server, can sometimes allow directory browsing. Consult your hosting provider’s documentation for specific instructions on configuring the web server to block directory listings. Verify the server configuration files (e.g., .htaccess, configuration files for Apache or Nginx) to ensure they don’t allow directory browsing. This may involve checking the `AllowOverride` directive in Apache or Nginx’s directives for directory browsing.
- File system errors or server-side issues can manifest as directory browsing problems. Check the server logs for errors related to the directory browsing disabler or related files. Contact your hosting provider for assistance if you suspect a server-side issue. Review the server logs for errors or warnings related to the directory browsing disabler or the related files.
Security Best Practices
Disabling directory browsing is a crucial step in WordPress security, but it’s just one piece of the puzzle. A robust security posture requires a multi-faceted approach that extends beyond simply preventing directory listings. Implementing additional security measures will significantly enhance the protection of your website and its data.
Protecting your WordPress site goes beyond simply disabling directory browsing. A comprehensive approach includes regular updates, strong passwords, robust account security, and a reliable firewall. These measures work together to create a more secure environment, minimizing the risk of vulnerabilities and potential attacks.
Regular Updates
Regularly updating WordPress core, plugins, and themes is paramount to maintaining security. Outdated software often contains known vulnerabilities that hackers can exploit. Updates patch these weaknesses, providing a crucial defense against threats. New versions often include performance improvements and bug fixes as well. It’s a critical practice for website owners to ensure their platforms remain secure and efficient.
Strong Passwords and Account Security
Using strong passwords is essential for protecting your WordPress account and, by extension, your website. A strong password is long, complex, and memorable. Avoid using easily guessable information like birthdates, names, or common phrases. Utilize a password manager to generate and store strong, unique passwords for all your accounts. Additionally, enable two-factor authentication (2FA) whenever possible.
This adds an extra layer of security, requiring a second verification step beyond a password. This significantly reduces the risk of unauthorized access.
Securing your WordPress site involves disabling directory browsing, a crucial step to prevent unauthorized access. This protects your site’s sensitive files and folders. Effective pest control marketing, like strategies used in pest control marketing more effective bug zapper hurricane pest control marketing more effective bug zapper hurricane , requires a similar strategic approach. Strong security measures are essential for any website, and disabling directory browsing is a fundamental part of that process.
Robust Firewall, How to disable directory browsing in wordpress
A robust firewall acts as a barrier between your website and the internet, blocking malicious traffic and suspicious activity. Firewalls monitor incoming and outgoing network requests, filtering out potentially harmful connections. They can detect and block common attack vectors, such as brute-force login attempts, SQL injection attempts, and other malicious activities. Employing a firewall provides an extra line of defense, safeguarding your website from unwanted intrusions.
A good firewall solution should be tailored to the specific needs of your website and its traffic volume.
Advanced Techniques (Optional)
Beyond the straightforward methods, several advanced techniques can further bolster WordPress security against directory browsing vulnerabilities. These techniques often involve custom code or specialized tools, offering more granular control and tailored solutions. This section explores alternative approaches and their implications.
Advanced techniques for disabling directory browsing often require a deeper understanding of server configurations and WordPress functionality. Implementing these methods can improve security but also potentially introduce complexity. Carefully evaluate the trade-offs before implementing any advanced solutions.
Custom Code Solutions
Custom code solutions provide a high degree of control over directory browsing prevention. They allow for specific rules and tailored responses to potential attacks. This approach requires familiarity with PHP and server configurations.
- Using .htaccess: .htaccess files offer a powerful way to control access to directories. Custom directives can be employed to prevent directory listings within specific directories. For instance, you can use directives to deny access to directories like `/wp-content/uploads/` or other sensitive areas.
- PHP Scripting: PHP scripts can be employed to dynamically block access to directories based on specific conditions or user roles. This provides a more nuanced way to manage directory access than using .htaccess alone. Examples include checking user permissions or IP addresses before allowing access.
- Custom Theme or Plugin Hooks: Modifying WordPress core files directly can sometimes offer greater control. However, this method is often discouraged due to potential conflicts with future WordPress updates. Carefully consider the impact on plugin compatibility before altering core files.
Web Application Firewalls (WAFs)
A web application firewall (WAF) acts as a security layer between your WordPress site and the internet. WAFs can detect and block malicious requests attempting to exploit directory browsing vulnerabilities. This is a proactive measure that can prevent a wide range of attacks, including directory traversal attempts.
- Functionality: WAFs inspect HTTP requests for malicious patterns, such as those used in directory traversal attacks. If a request matches a predefined rule, the WAF can block the request before it reaches your WordPress site.
- Configuration: Proper configuration is crucial. Rules should be carefully selected to block only malicious requests while allowing legitimate traffic. This involves understanding the specific vulnerabilities your site faces and the types of requests associated with them.
- Integration: WAFs can be integrated with your web hosting provider or you can use a third-party service. The integration process may vary depending on the chosen WAF solution.
Comparison of Advanced Techniques
Different methods offer varying levels of control and complexity. Careful consideration of your specific needs is essential.
| Technique | Pros | Cons |
|---|---|---|
| .htaccess | Simple to implement, often sufficient for basic needs. | Limited flexibility, less effective against sophisticated attacks. |
| PHP Scripting | Highly customizable, offers greater control over access. | Requires more technical expertise, can be more complex to maintain. |
| Custom Theme/Plugin Hooks | Highly granular control over directory access. | Significant risk of conflicts with future updates, potentially breaking functionality. |
| WAF | Proactive protection, can block a broad range of attacks. | Requires a subscription or dedicated service, might introduce latency. |
Closure
By following the steps Artikeld in this comprehensive guide, you’ll effectively disable directory browsing on your WordPress site, bolstering its security posture. Remember, regular updates and strong passwords are equally important components of a well-rounded security strategy. Protecting your website from directory browsing vulnerabilities is a vital step in ensuring its safety and reliability.