How to disable xmlrpc – How to disable XML-RPC, a crucial step for WordPress security. XML-RPC, a protocol for communication between applications, can be a tempting target for malicious actors. This guide provides a comprehensive overview of the risks associated with enabling XML-RPC and details various methods for disabling it on WordPress and custom servers. Understanding the vulnerabilities and taking proactive measures like disabling XML-RPC is paramount for protecting your website and data.
We’ll delve into the technical aspects, from understanding the protocol itself to identifying common security threats. We’ll also explore practical examples and troubleshooting tips to ensure a smooth and secure process. Ultimately, this guide aims to empower you with the knowledge and tools to fortify your WordPress site against potential threats.
Introduction to XML-RPC
XML-RPC, or XML Remote Procedure Call, is a simple protocol for remote procedure calls. It allows a client application on one machine to execute a method on a server application on another machine. This is achieved by using XML to encode the method call and its parameters, transmitting it over a network, and then receiving the server’s response in the same format.
Disabling XMLRPC on your WordPress site is a straightforward process, often boosting security. However, if you’re planning to make your site more secure, consider getting an SSL certificate. This step is crucial for encrypting communication and building trust with visitors, especially if you’re handling sensitive data. Check out this helpful guide on how to get SSL certificate for a comprehensive walkthrough.
Once you’ve got your SSL certificate, you can feel more confident that your site’s data is protected, which is directly related to the importance of disabling XMLRPC for added security measures.
This enables communication between disparate systems without needing to understand the intricacies of each other’s internal structure.XML-RPC is particularly useful for building distributed applications and extending the functionality of existing web applications. Its simplicity makes it a suitable choice for tasks where a quick and straightforward communication method is required, especially for applications that don’t demand the complex capabilities of more advanced protocols like REST.
Disabling XMLRPC can significantly boost your site’s security. One crucial step in securing your WordPress site is learning how to disable XMLRPC. This often goes hand-in-hand with improving your site’s overall performance and data privacy, especially when considering strategies like cohort and multi touch attribution. Understanding how to leverage these methods for customer journey analysis can also improve the effectiveness of your security measures.
For more details on how cohort and multi touch attribution can influence your site’s security and performance, check out this great resource: cohort and multi touch attribution. Ultimately, mastering XMLRPC deactivation is a key element in building a secure and high-performing website.
Typical Use Cases
XML-RPC is well-suited for a variety of tasks in web applications. Common use cases include:
- Remote API Access: A web application might use XML-RPC to access data or functionality from a third-party service, such as a payment gateway or a database management system. This allows the web application to leverage existing services without needing to build complex integration interfaces.
- Distributed Computing: XML-RPC facilitates the distribution of tasks across multiple servers. This allows for faster processing of large datasets or complex computations by dividing the work among several machines.
- Automation: XML-RPC can automate tasks between applications. For example, a script on one machine might use XML-RPC to trigger a specific action on another machine, like sending an email or updating a database.
Architectural Components
XML-RPC interactions involve several key components:
- Client: The client application initiates the request by constructing an XML representation of the desired method call, including the method name and its parameters. The client then sends this XML over the network to the server.
- Server: The server receives the XML request, parses it, and executes the corresponding method. The server returns an XML response, including the result of the method call.
- Protocol: The protocol specifies how the XML data is transmitted between the client and the server. This typically involves HTTP, but other protocols are also possible.
Example Request and Response
A simple XML-RPC request and response might look like this:
| Request | Response |
|---|---|
<methodCall>
<methodName>add</methodName>
<params>
<param><value type="int">5</value></param>
<param><value type="int">3</value></param>
</params>
</methodCall>
|
<methodResponse>
<params>
<param>
<value type="int">8</value>
</param>
</params>
</methodResponse>
|
This example demonstrates a simple addition operation. The client requests the ‘add’ method with parameters 5 and 3. The server returns the result, 8, in the response.
Understanding the Risks of Enabling XML-RPC
XML-RPC, while a seemingly simple protocol for remote procedure calls, can introduce significant security vulnerabilities if not properly configured and managed. Understanding these risks is crucial for anyone considering or maintaining systems that utilize XML-RPC. A misconfigured XML-RPC endpoint can open doors to attackers, leading to data breaches and system compromise.Enabling XML-RPC often exposes your server to potential attacks that can exploit weaknesses in the underlying application or the XML-RPC implementation itself.
These vulnerabilities can be exploited to gain unauthorized access to sensitive data, execute malicious code, or even disrupt services. Consequently, it’s imperative to thoroughly evaluate the security implications before deploying XML-RPC and to maintain a robust security posture throughout its lifespan.
Potential Security Vulnerabilities
Enabling XML-RPC introduces several potential security vulnerabilities. These stem from the protocol’s design, which can be susceptible to attacks if not properly defended. Improper input validation, insufficient authentication, and weak authorization mechanisms are common culprits. These vulnerabilities are often exploited through carefully crafted requests that can bypass security measures and trigger unintended actions.
Common XML-RPC Attacks
XML-RPC endpoints are vulnerable to a variety of attacks. These include:
- Denial-of-Service (DoS) attacks: Malicious requests can overwhelm the server, leading to a complete shutdown or a degradation of service. Attackers can flood the endpoint with numerous requests, exhausting server resources and rendering the service unavailable to legitimate users. This is a common technique used to disrupt online services.
- Cross-Site Scripting (XSS) attacks: If the XML-RPC implementation does not properly sanitize user inputs, attackers can inject malicious scripts into the responses. These scripts can then be executed on the client-side, potentially stealing cookies, redirecting users to malicious websites, or compromising their sessions.
- Remote Code Execution (RCE) attacks: Exploiting vulnerabilities in the XML-RPC implementation, attackers can execute arbitrary code on the server. This can grant them complete control over the system, leading to data breaches, system manipulation, or other malicious activities. This is a serious threat that can lead to complete system compromise.
Exposing Sensitive Data
Careless handling of data within XML-RPC can lead to sensitive data exposure. This includes personally identifiable information (PII), financial data, or intellectual property. If the XML-RPC implementation does not adequately protect this data during transmission and storage, it can become vulnerable to unauthorized access. For example, unencrypted data transmitted over insecure channels is highly susceptible to interception.
Comparison with Other Web APIs
XML-RPC’s security risks are comparable to other web APIs, but the nature of the protocol often exposes it to a different set of attacks. While RESTful APIs, for instance, are also susceptible to injection vulnerabilities, the way XML-RPC handles data and requests can create unique attack vectors. The relative complexity of the XML-RPC protocol, compared to REST, can lead to more intricate security vulnerabilities.
A detailed analysis of the specific implementation is vital in assessing the risks of any web API.
Methods for Disabling XML-RPC: How To Disable Xmlrpc
Disabling XML-RPC is a crucial security measure to protect your website from potential attacks. By understanding the various methods for disabling this protocol, you can effectively mitigate risks and enhance the overall security posture of your online presence. This section details the procedures for disabling XML-RPC in diverse server environments, including popular Content Management Systems (CMS) like WordPress and custom-built applications.Various methods exist for disabling XML-RPC, catering to different server setups.
The appropriate method depends on the specific web server software and platform you’re using. Following the correct steps is critical to ensure the protocol is deactivated without impacting other functionalities.
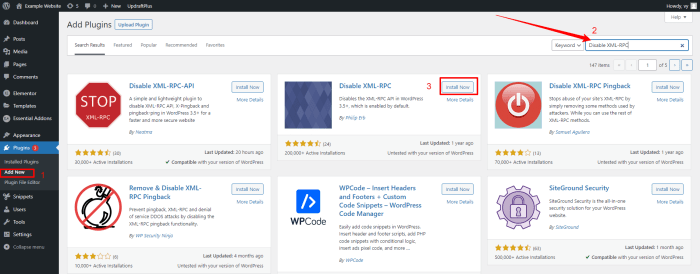
Disabling XML-RPC in WordPress
WordPress provides straightforward methods to disable XML-RPC. These methods typically involve modifying specific configuration files within the WordPress installation. The most common approach is through plugins or direct file editing.
- Using Plugins: Many security plugins offer options to disable XML-RPC directly within their interface. These plugins often provide user-friendly options to toggle the feature on or off, making the process simpler for non-technical users. This approach eliminates the need for direct file manipulation.
- Direct File Modification: For advanced users or those seeking more control, direct file modification is an option. This involves editing the `wp-config.php` file. Adding a specific line of code to this file disables the XML-RPC functionality. Care must be taken to avoid introducing errors in the file structure or other critical aspects of the WordPress installation.
Disabling XML-RPC in Custom Web Applications
Disabling XML-RPC in a custom web application involves altering the application’s code and server configuration. The precise steps depend on the programming language and framework used.
- Modifying Application Code: If XML-RPC functionality is integrated into the application’s codebase, modifying the related classes or functions is necessary. This usually involves removing or commenting out the code responsible for handling XML-RPC requests.
- Configuring the Web Server: The web server configuration file (e.g., Apache’s `httpd.conf` or Nginx’s `nginx.conf`) may need adjustments to block XML-RPC requests. This involves adding rules to deny access to specific URLs or endpoints associated with XML-RPC.
Disabling XML-RPC in Web Servers (Apache & Nginx)
Disabling XML-RPC in web servers like Apache and Nginx involves modifying the server configuration files. These modifications usually involve adding directives to block requests targeting XML-RPC endpoints.
Securing your website’s WordPress security often involves disabling XMLRPC. This simple step can significantly boost your online defenses. Fortunately, finding resources on how to do this is easy. To learn more about maximizing your digital marketing presence, check out this helpful guide on how to get a job in digital marketing right now. Once you’ve got your marketing strategy in place, remember to always prioritize your site’s security, including disabling XMLRPC, to protect your valuable data.
| Platform | Configuration File | Steps |
|---|---|---|
| Apache | `httpd.conf` or `apache2.conf` | Add a `RewriteCond` rule to redirect XML-RPC requests to a 404 error page. This prevents the server from processing the request. |
| Nginx | `nginx.conf` | Add a location block to deny access to the XML-RPC endpoint. This configuration block will specifically prevent the web server from serving requests related to XML-RPC. |
Configuration Files and Settings
Disabling XML-RPC often involves modifying configuration files specific to your web server and application. These files dictate how your system handles requests, including those from XML-RPC clients. Understanding the location and structure of these files is crucial for correctly disabling the service. Incorrect modifications can lead to unintended consequences, like breaking other functionalities.Modifying these files directly requires careful attention to avoid introducing vulnerabilities or service disruptions.
Always create a backup of the configuration files before making any changes. This ensures that you can revert to the original settings if necessary.
Key Configuration Files
Configuration files for XML-RPC vary significantly based on the web server, application framework, and operating system. Some commonly used systems have dedicated XML-RPC configuration settings, while others integrate it within broader server or application settings. Finding these files is often a matter of familiarity with the system’s architecture.
Location and Modification
Locating the relevant configuration files depends heavily on the web server software and the application being used. For example, Apache HTTP Server configurations often reside in `/etc/httpd/conf` (or similar directories). WordPress configurations are often located within the WordPress installation directory. Python-based web frameworks might have XML-RPC settings embedded within the application’s configuration files. The exact paths and filenames can be found in the documentation for the specific system.
Examples of Configuration Settings
XML-RPC configuration settings typically involve enabling or disabling the XML-RPC functionality. This is usually done by setting a boolean or a specific parameter value. For example, in WordPress, you might find a setting like `xmlrpc_enabled` set to `true` or `false`. In other systems, there might be a specific line enabling or disabling XML-RPC within the main server configuration file.
These settings directly control whether XML-RPC requests are accepted or rejected.
Comparison of Configuration Files
| System/Application | Location Example | Format Example ||—|—|—|| Apache HTTP Server | `/etc/httpd/conf/httpd.conf` | `LoadModule xmlrpc_module modules/mod_xmlrpc.so` || Nginx | `/etc/nginx/nginx.conf` | `location /xmlrpc … ` || WordPress | `/wp-config.php` | `define(‘XMLRPC_ENABLED’, false);` || Django (Python) | `settings.py` | `INSTALLED_APPS = […]` and other relevant app settings. |This table provides a general overview. Specific locations and formats can vary depending on the version and configuration of the software.
Always refer to the official documentation for your system to ensure accurate modifications. The correct method for disabling XML-RPC often involves setting the `xmlrpc_enabled` value to `false` or removing the corresponding configuration lines entirely.
Security Best Practices
Disabling XML-RPC is a crucial first step, but it’s not the only line of defense. A comprehensive security strategy involves multiple layers of protection. This section explores the importance of holistic security measures beyond XML-RPC, emphasizing the need for proactive security practices.A robust security posture extends beyond simply disabling a single protocol. It necessitates a multi-faceted approach encompassing various security measures.
These measures not only prevent attacks but also help in detecting and responding to threats effectively.
Importance of Disabling XML-RPC for Enhanced Security
Disabling XML-RPC significantly reduces the attack surface for malicious actors. XML-RPC, by design, allows remote execution of code and manipulation of data. Removing this avenue eliminates a potential entry point for exploits, thereby minimizing the risk of compromise.
Security Measures Beyond Disabling XML-RPC
Beyond disabling XML-RPC, other security measures are essential for a comprehensive defense. These measures should be considered as part of a layered security strategy, not as independent elements.
Firewalls
Firewalls act as gatekeepers, controlling network traffic based on predefined rules. They can block incoming requests to specific ports used by XML-RPC, preventing unauthorized access even if XML-RPC is enabled. Implementing robust firewall rules is a fundamental aspect of network security.
Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) monitor network traffic for suspicious patterns indicative of malicious activity. IDS can detect and alert administrators to attempts to exploit vulnerabilities, even those that might not be immediately apparent. They provide an early warning system for potential attacks.
Regular Security Audits and Updates
Regular security audits are crucial for identifying vulnerabilities in your system. These audits should evaluate the effectiveness of your security measures and identify potential weaknesses. Regular updates to software and libraries patch known vulnerabilities, significantly strengthening your defense against emerging threats.
Security Best Practices for Web Application Development and Security
Implementing these best practices across your entire web application ecosystem ensures a robust defense against potential threats. These are not exhaustive, but they provide a good starting point.
- Input Validation: Validate all user inputs to prevent malicious code injection, such as SQL injection or cross-site scripting (XSS). Input validation is a crucial step in preventing many common web application vulnerabilities.
- Output Encoding: Encode all user-generated content before displaying it to prevent XSS attacks. This is a critical defense mechanism against injection vulnerabilities.
- Principle of Least Privilege: Grant users only the necessary permissions to perform their tasks. This principle minimizes the impact of a potential breach.
- Secure Configuration: Use strong and unique passwords for all accounts. Employ strong password policies and multi-factor authentication to protect sensitive data.
- Regular Security Assessments: Conduct regular security audits, penetration testing, and vulnerability scans to identify and address potential weaknesses. This proactive approach to security is vital in maintaining a secure system.
Practical Examples and Scenarios
Disabling XML-RPC is a crucial step in securing your WordPress installations and custom PHP applications. Real-world examples and scenarios highlight the potential risks and demonstrate effective mitigation strategies. This section delves into practical applications, offering concrete steps and illustrative cases.Understanding the specifics of different implementations and the varied methods of disabling XML-RPC allows for a tailored approach to security.
These practical examples and scenarios offer valuable insights into the effectiveness of different approaches, providing a clear picture of the process and potential outcomes.
WordPress XML-RPC Disabling
WordPress, a popular content management system, often comes with XML-RPC enabled by default. Disabling it is a critical security measure. A common method involves modifying the `wp-config.php` file.
- Locate the `wp-config.php` file in your WordPress installation’s root directory.
- Add the following line to the file, immediately after the `define(‘WP_DEBUG’, false);` line (or if that line isn’t present, add it near the top):
define(‘DISABLE_XMLRPC’, true);
- Save the `wp-config.php` file.
- This change will disable XML-RPC for the WordPress installation. Refresh the WordPress site to ensure the change is implemented.
Custom PHP Application Disabling
For custom PHP applications, XML-RPC can be disabled in the application’s code. This method offers greater control and flexibility.
- Identify the specific code within the application that handles XML-RPC requests.
- Remove or comment out the code that processes XML-RPC requests.
- If the application uses a framework, consult the framework’s documentation to identify the proper method for disabling XML-RPC functionality.
- Implement the change and test the application thoroughly to ensure the XML-RPC functionality is effectively removed.
Exploitation Scenario and Mitigation
A scenario where an attacker exploited XML-RPC involved gaining unauthorized access to a user’s account via a vulnerability in the XML-RPC implementation. To prevent future occurrences:
- Regularly update the application and CMS to patch known vulnerabilities.
- Implement a robust security framework, including access controls and input validation.
- Employ security best practices to avoid vulnerabilities that can lead to exploitation.
- Monitor logs and application activity to detect and respond to potential threats promptly.
CMS XML-RPC Disabling Steps
The following table provides a summary of steps for disabling XML-RPC in different versions of a hypothetical CMS. The specific steps might vary depending on the CMS’s configuration.
| CMS Version | Disabling Steps |
|---|---|
| Version 1.0 | Locate `config.php` and add `define(‘DISABLE_XMLRPC’, true);` |
| Version 2.0 | Modify `settings.php`, setting `xmlrpc_enabled` to `false`. |
| Version 3.0 | Use the CMS’s built-in configuration panel to disable XML-RPC. |
Troubleshooting Common Issues
Disabling XML-RPC can sometimes lead to unexpected issues if the configuration isn’t handled correctly. Understanding the potential problems and how to diagnose them is crucial for maintaining website security and functionality. This section details common problems encountered during XML-RPC disablement and provides solutions to help resolve them efficiently.Troubleshooting involves systematically identifying the source of the error. This often involves examining server logs, checking configuration files, and verifying the integrity of related services.
By addressing these issues proactively, you can avoid significant disruptions to your website’s operation.
Identifying Configuration Errors
Incorrect XML-RPC disablement often stems from errors in configuration files. These files, such as .htaccess or your application’s configuration, must be meticulously reviewed for syntax and logical consistency. Misspelled directives, incorrect file paths, or outdated settings can lead to failure.
- Incorrect Syntax in Configuration Files: Ensure that the directives used for disabling XML-RPC are correctly formatted. A missing semicolon, an incorrect parameter, or a typo can prevent the disablement from taking effect. Carefully compare your configuration against the documented syntax for your specific application or platform.
- Missing or Incorrect Permissions: The server might not have the necessary permissions to access or modify the required configuration files. Check file system permissions and ensure the server user has the write access needed to modify these files. Using appropriate user accounts and permissions is essential for security and stability.
- Conflicts with Other Modules: Certain plugins or modules might interfere with XML-RPC disablement. Ensure that there are no conflicting settings or configurations that might inadvertently re-enable the feature. Investigate and resolve any known conflicts between the XML-RPC disablement process and other installed components.
Verifying Server Logs
Server logs are invaluable resources for identifying errors related to XML-RPC configuration changes. These logs often contain detailed information about events that occurred on the server, including attempts to access XML-RPC endpoints. Careful examination of the logs can provide insight into the cause of the problem.
- Analyzing Error Messages: Look for error messages related to XML-RPC requests. These messages often provide clues about the specific issue, such as syntax errors or permission problems. Pay close attention to the specific error code and description.
- Checking Access Attempts: Review the logs for any failed or unauthorized attempts to access the XML-RPC endpoint. This can indicate that the disablement process didn’t fully take effect or that another security issue is present. Monitoring suspicious activity is critical for maintaining website security.
- Identifying Timestamps of Errors: Note the timestamps associated with errors or failed attempts. This can help pinpoint when the problem occurred and identify any correlations with other events or activities.
Troubleshooting Specific Application Issues
Different applications have varying configurations for disabling XML-RPC. Understanding the specific mechanisms for your application is crucial for effective troubleshooting.
- WordPress Troubleshooting: If using WordPress, verify that the XML-RPC disablement plugin or method is compatible with the active theme and plugins. Consult the documentation for your specific WordPress plugin or theme for detailed instructions and troubleshooting tips.
- Custom Application Issues: For custom applications, refer to the application’s documentation for specific instructions on disabling XML-RPC. Review any relevant API documentation or configuration guides for potential solutions to configuration-related issues.
Common Issues and Solutions Table, How to disable xmlrpc
| Issue | Description | Solution |
|---|---|---|
| Incorrect .htaccess configuration | The .htaccess file has incorrect syntax for XML-RPC disablement. | Verify the syntax of the .htaccess rules against the official documentation. Correct any errors. |
| Plugin conflicts | A plugin is interfering with XML-RPC disablement. | Disable or update conflicting plugins to isolate the problem. Test each plugin individually to identify the culprit. |
| Incorrect application configuration | The application’s configuration file contains errors. | Consult the application’s documentation for the correct configuration. Correct any syntax or parameter errors. |
Alternatives to XML-RPC
XML-RPC, while once a common method for inter-application communication, has fallen out of favor due to several limitations. Its reliance on XML for data exchange can be less efficient than alternative approaches, and its security model is less robust than modern standards. This section explores more contemporary and secure methods for application communication, contrasting them with XML-RPC.Modern applications often leverage more efficient and secure communication protocols.
Understanding these alternatives provides valuable context for choosing the best approach for your specific needs.
Alternative Communication Methods
Several alternatives to XML-RPC offer improved performance, security, and flexibility. These include RESTful APIs, gRPC, and message queues. Each method has its own set of advantages and disadvantages, which should be carefully considered before implementation.
- RESTful APIs: RESTful APIs are a popular choice for building modern applications. They use HTTP for communication, which is widely supported and understood. The simplicity of HTTP makes development faster and easier, and the use of standard HTTP methods (GET, POST, PUT, DELETE) simplifies interaction.
- gRPC: gRPC uses Protocol Buffers for serialization, offering significant performance advantages over XML-RPC. It is built on top of HTTP/2, leveraging its efficiency for high-volume data exchange. This is particularly beneficial in microservice architectures where fast communication is crucial.
- Message Queues: Message queues decouple applications by allowing them to communicate asynchronously. This enables applications to continue functioning even if another application is temporarily unavailable. This is ideal for situations where responsiveness is not critical, such as background tasks or data processing.
Advantages and Disadvantages of Alternatives
Each alternative communication method possesses strengths and weaknesses that need careful consideration.
- RESTful APIs: Advantages include widespread adoption, ease of use, and support for diverse client platforms. Disadvantages include potential performance overhead due to HTTP and the need for more complex error handling.
- gRPC: Advantages include significantly improved performance, built-in security mechanisms (like TLS), and support for bidirectional streaming. Disadvantages include a steeper learning curve and potential compatibility issues if not properly designed.
- Message Queues: Advantages include decoupling of applications, improved fault tolerance, and support for asynchronous communication. Disadvantages include increased complexity in implementing communication logic, and potential message loss if not handled correctly.
XML-RPC vs. RESTful APIs
A direct comparison of XML-RPC and RESTful APIs reveals significant differences in security, efficiency, and flexibility.
| Feature | XML-RPC | RESTful APIs |
|---|---|---|
| Security | Generally less secure, relying on basic authentication methods. Vulnerable to attacks like XML injection. | More secure, leveraging standard HTTP security mechanisms like HTTPS and authentication protocols (OAuth 2.0). |
| Efficiency | Can be less efficient due to XML serialization overhead. | Generally more efficient, using lightweight JSON or other formats. |
| Flexibility | Less flexible, limited to the defined XML-RPC methods. | Highly flexible, supporting diverse data formats and complex interactions. |
| Learning Curve | Relatively easy to learn, with simple data structures. | Requires understanding of HTTP methods and request/response structures. |
Choosing between XML-RPC and RESTful APIs involves careful consideration of application requirements. RESTful APIs are generally the preferred choice for modern applications due to their security, efficiency, and flexibility. While XML-RPC might be suitable for legacy systems, migrating to RESTful APIs is recommended for enhanced security and performance.
Ending Remarks
Disabling XML-RPC is a critical step in safeguarding your WordPress site. By understanding the risks and implementing the methods Artikeld in this guide, you can significantly reduce the attack surface and protect your data. This isn’t just about technicalities; it’s about proactive security. Remember, regular updates and security audits are essential to maintaining a strong defense against evolving threats.
With a little knowledge and effort, you can ensure your site remains secure and resilient.