How to allow users to invite their friends to register in WordPress is a crucial aspect of community building. This guide will walk you through the entire process, from setting up the invitation system to handling registrations and security. We’ll explore various methods, plugins, database interactions, and user experience considerations to ensure a seamless and secure invitation process.
We’ll dive into different approaches, including email, social media, and custom links, evaluating their strengths and weaknesses. We’ll also discuss popular WordPress plugins to streamline the process and provide guidance on configuring them. Security is paramount, and we’ll cover crucial aspects like data validation, error handling, and preventing spam and malicious activity.
User Invitation Mechanisms
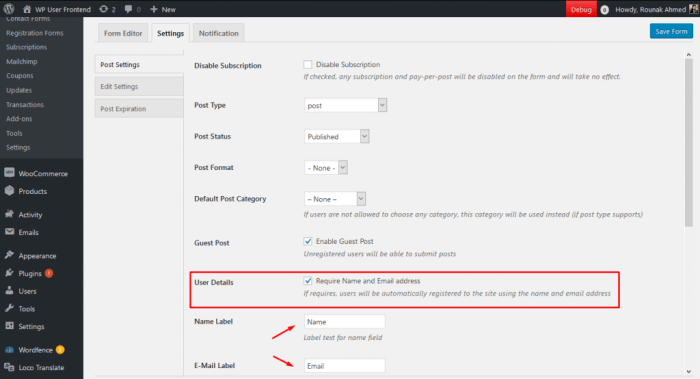
Inviting friends to register on your WordPress site is a crucial aspect of user growth. A robust invitation system fosters community engagement and encourages user expansion. Effective invitation mechanisms should be simple for users and secure to protect the site from abuse. This section details the methods, implementation, and security considerations of creating a user invitation system within WordPress.The success of a WordPress site hinges on the ability to attract and retain users.
Want to boost user sign-ups on your WordPress site? Enabling friend invitations is a great way to grow your community. However, while you’re building your website’s user base, consider the complex legal landscape around generative AI, like the issues raised by the U.S. Copyright Office in their recent report on generative AI. You’ll need to ensure any content generated by your users or your website doesn’t infringe on existing copyrights.
This awareness will help you design a robust user-invitation system that’s both user-friendly and legally sound.
A user invitation system provides a clear path for existing users to bring their networks into the fold. It’s a powerful tool to increase traffic and participation.
Invitation Methods
A well-designed invitation system offers multiple avenues for users to invite friends. This flexibility accommodates various user preferences and encourages participation from diverse user groups. Methods range from simple email invitations to more sophisticated social media integrations.
- Email Invitations: Email remains a cornerstone of communication, and email invitations provide a straightforward and familiar approach. Users can easily share invitation links with friends via email, facilitating a direct connection. This method is widely accessible and often the first choice for users.
- Social Media Invitations: Leveraging social media platforms extends the reach of invitations. Integration with social media APIs allows users to invite friends directly through their preferred platforms. This method can tap into a vast user base but requires careful handling of API access and user permissions.
- Custom Links: Custom links offer flexibility, enabling the creation of unique invitation links for specific users or groups. These links can be tailored with specific parameters, such as referral bonuses or personalized content, boosting user engagement. Careful management of these links is essential to prevent misuse and maintain site security.
Creating an Invitation System in WordPress
Implementing an invitation system within WordPress involves several key steps. First, you need a plugin or custom code to handle the invitation process. This code should validate user inputs and ensure the security of the invitation links.
- Plugin Integration: Numerous WordPress plugins offer invitation features, often simplifying the process of integrating these tools. These plugins often handle the generation of invitation links, database management, and user account creation, freeing up development time for other aspects of the site.
- Custom Code Development: For greater control, a custom solution allows tailoring the invitation system to specific site requirements. This method provides maximum flexibility but requires more development effort and expertise. This approach allows for advanced features, but also poses a greater risk of errors or vulnerabilities if not implemented meticulously.
User Interface Design
The user interface for sending invitations should be intuitive and user-friendly. It should incorporate clear input fields for friend email addresses or social media handles, allowing users to easily invite their contacts.
- Input Fields: The interface should have designated input fields for email addresses and/or social media handles. These fields should be clearly labeled and provide validation to prevent invalid or malicious input.
- Clear Instructions: Clear instructions on how to invite friends are essential to avoid user confusion. The instructions should be readily available on the invitation page and ideally, integrated with the WordPress dashboard.
Security Considerations
Protecting the invitation system from spam or malicious activity is crucial. Implementing robust security measures ensures the integrity of the site and the positive experience for users.
- Spam Prevention: Mechanisms for detecting and preventing spam submissions should be in place. This includes rate limiting, email address validation, and potentially CAPTCHA verification to reduce spam attempts.
- Malicious Activity: The system should be designed to detect and prevent malicious activity. This involves regularly monitoring for suspicious invitation links and user behavior to minimize risks. Regular security audits are essential to maintain the integrity of the invitation system.
User Journey Flow Chart
[A flow chart illustrating the user journey from invitation to registration is omitted here as it cannot be displayed in plain text format.]
Comparison of Invitation Methods
A table outlining the advantages and disadvantages of different invitation methods is provided below.
| Method | Pros | Cons |
|---|---|---|
| Simple, widely used, cost-effective | Can be ignored/spammed, limited reach | |
| Social Media | Wider reach, targeted invitations | Requires API integration, potential privacy concerns |
| Custom Links | Flexibility, potential for personalization | Requires careful handling, potential for misuse |
WordPress Plugin Options
WordPress plugins offer a streamlined approach to implementing user invitation features. These tools often handle the complexities of email invitations, user registration, and permission management, saving significant development time for website owners. They provide pre-built functionality, reducing the need for custom coding and allowing focus on core website content.
Identifying Suitable Plugins
Several WordPress plugins excel at facilitating user invitations. These plugins vary in their features, pricing, and complexity. Careful selection is crucial for optimal integration and compatibility with your existing website setup. Thorough research into available options is recommended before committing to a particular plugin.
Plugin Integration Process
Integrating a chosen plugin typically involves downloading, installing, and activating it within your WordPress dashboard. Following the plugin’s specific instructions is crucial for proper configuration. Often, plugins offer customization options to tailor the invitation process to your website’s unique requirements. These options may include specifying the email template, invitation message, or the user roles assigned to invited users.
Comparing Plugin Functionalities
Different plugins cater to varying needs and offer different levels of customization. Essential features to consider when comparing plugins include the ability to personalize invitation emails, the options for controlling user roles, and the support for bulk invitations. Some plugins may offer advanced features like managing user registration through a separate registration form. Other plugins might be optimized for particular website types, such as those focused on membership sites or forums.
Assessing these functionalities is critical in selecting the right plugin.
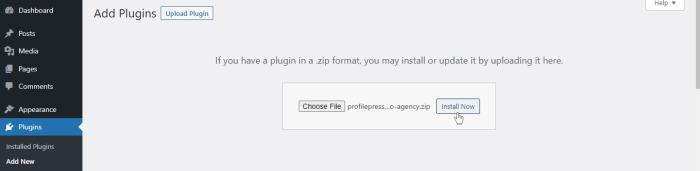
Demonstrating Installation and Configuration
To illustrate, let’s consider the “User Invite” plugin. After downloading the plugin’s zip file, navigate to the “Plugins” section within your WordPress dashboard. Click on “Add New,” select “Upload Plugin,” and choose the downloaded zip file. After installation, activate the plugin. Typically, the plugin’s settings page will guide you through configuring the invitation process.
This might involve setting up email templates, specifying the invitation message, or defining user roles for the invited users. It is crucial to consult the plugin’s documentation for specific steps.
Summary of Popular Plugins
| Plugin Name | Key Features | Pros | Cons |
|---|---|---|---|
| User Invite | Personalized email invitations, customizable roles, bulk invitations | Easy to use, well-documented, offers flexibility in customization | Limited advanced features compared to some other plugins |
| WP User Frontend | Simplified user registration, multiple registration forms, and user management | Good for sites with complex user registration needs, offers robust user management | Can be more complex to configure compared to simpler plugins |
| MemberPress | Membership site management, user roles, and payment integrations | Ideal for membership-based websites, offers comprehensive membership features | Often more expensive and complex to set up |
Database Interactions
Storing user invitation data within the WordPress database is crucial for managing the invitation process efficiently. This involves creating specific tables to house invitation details, ensuring data integrity, and enabling easy retrieval and updates. Proper database design facilitates streamlined user management and a smooth user experience.Effective data organization within the WordPress database ensures the smooth operation of the user invitation system.
A well-structured database allows for efficient retrieval and modification of invitation records, contributing to a user-friendly experience.
Table Structure for Invitations
Careful planning of the database structure is essential to maintaining data integrity and enabling efficient queries. The table structure for storing invitation details should include relevant information, such as the sender, recipient, and status of the invitation.
- The invitations table will store the invitation details. Key columns include:
invitation_id(INT, AUTO_INCREMENT, PRIMARY KEY): Unique identifier for each invitation.sender_user_id(INT): The ID of the user who sent the invitation.recipient_user_id(INT): The ID of the user who received the invitation.invitation_code(VARCHAR): A unique alphanumeric code for the invitation, used for verification.status(ENUM(‘pending’, ‘accepted’, ‘rejected’)): Tracks the status of the invitation.timestamp(TIMESTAMP): Records the time the invitation was sent.
User Table Considerations
The users table, already present in WordPress, will be crucial for storing information about the users involved in the invitation process.
- Ensure the users table has columns to hold essential user information, such as user IDs, email addresses, and other relevant data.
SQL Queries for Retrieving and Updating Data
Efficient SQL queries are necessary for retrieving and updating invitation data. These queries should be designed for optimal performance and security.
- Retrieving Pending Invitations for a User:
“`sql
SELECT
–
FROM invitations
WHERE recipient_user_id = 123 AND status = ‘pending’;
“`
This query retrieves all pending invitations for the user with ID 123. Adjusting the `recipient_user_id` will target specific users. - Updating Invitation Status:
“`sql
UPDATE invitations
SET status = ‘accepted’
WHERE invitation_id = 456;
“`
This SQL statement updates the status of invitation with ID 456 to ‘accepted’. Replace `456` with the appropriate invitation ID.
Verifying Recipient Existence
Validating the recipient’s existence within the database is crucial to prevent errors and ensure the invitation process functions correctly.
- A crucial step is to verify that the recipient user exists in the users table before sending or processing an invitation.
- Using a query to check if a user with the specified ID exists can prevent issues like sending invitations to non-existent users.
“`sql
SELECT COUNT(*)
FROM users
WHERE ID = 789;
“`
This query checks if a user with ID 789 exists in the users table.The result will be 1 if the user exists and 0 otherwise. This check is vital to avoid errors during the invitation process.
User Registration Process
The user registration process is a critical part of the friend invitation system. A smooth and intuitive registration flow is essential for a positive user experience and encourages adoption of the feature. This section details the steps involved, focusing on automation, user experience, and error handling.The registration process after receiving an invitation should be streamlined to minimize friction for the invited user.
Automation of account creation upon successful registration saves the system administrator time and effort while ensuring a consistent and predictable outcome.
Registration Steps After Invitation, How to allow users to invite their friends to register in wordpress
The process should be straightforward and clear. Users should receive a personalized invitation, typically via email or a dedicated link, containing details about the invitation and instructions on how to proceed.
- Step 1: Accessing the Registration Page: The user clicks on the invitation link, which directly takes them to a registration page specifically designed for invited users. This avoids confusion and ensures a tailored experience.
- Step 2: Entering Registration Information: The user fills out the necessary registration form with details such as username, password, and email address. Crucially, this form should be tailored to the invitation and should pre-populate any relevant information where possible.
- Step 3: Confirmation and Account Creation: Upon successful form submission, the system validates the information. If valid, the user’s account is automatically created in the WordPress database. A confirmation message is displayed, indicating the account creation and any next steps.
- Step 4: Login and Dashboard Access: The user is presented with login credentials and is directed to the WordPress dashboard. The dashboard should welcome the user and provide instructions or tutorials if appropriate. This guides the user to familiarize themselves with the platform and its features.
Automatic Account Creation
Automated account creation upon successful registration is highly recommended for efficiency and consistency. This eliminates manual intervention, reduces errors, and ensures that the system functions reliably.
- Database Integration: A critical part of the process involves seamlessly integrating the invitation data into the WordPress user database. This data should be validated and normalized to avoid data integrity issues.
- WordPress API Usage: The plugin should leverage WordPress’s built-in API for user creation. This ensures compatibility and reduces the risk of conflicts with existing WordPress functionalities.
- Data Validation: Rigorous data validation is essential. The system should validate inputs, ensuring that user data meets the required standards and conforms to the expected format. This safeguards the database against invalid data and prevents future issues.
User Experience During Registration
A smooth registration process contributes significantly to a positive user experience. The user interface should be intuitive and easy to navigate.
- Clear Instructions: Provide clear and concise instructions at each step of the registration process. This avoids user confusion and ensures that the process is easily understood.
- Progressive Disclosure: Only request the necessary information at each stage. This prevents overwhelming the user with a lengthy form.
- Feedback Mechanisms: Provide timely and informative feedback to the user throughout the process. This includes error messages and confirmation messages to keep the user informed about the status of their registration.
Handling Invalid or Duplicate Invitations
Error handling is critical to ensure a reliable and user-friendly experience. Invalid or duplicate invitations should be managed gracefully to prevent errors and frustration.
- Invitation Validation: The system should validate the invitation’s authenticity before proceeding with the registration process. Invalid invitations should be flagged and the user notified.
- Duplicate Invitation Detection: The system should check for duplicate invitations to prevent the creation of multiple accounts for the same user. Duplicate invitations should be rejected, and the user informed accordingly.
- Error Reporting: Appropriate error messages should be displayed to the user. These messages should be clear and concise, explaining the reason for the rejection and providing guidance on how to proceed.
User Story: Registration Flow
A user receives an email invitation to register on the platform. The user clicks on the invitation link, which takes them directly to a registration page. The page pre-populates some fields with data from the invitation. The user fills in the remaining information and submits the form. Upon successful submission, a confirmation message appears, and the user’s account is automatically created.
Want to make it easier for your WordPress users to invite friends? It’s surprisingly straightforward to set up a friend-referral system. However, when tackling international PPC campaigns, you’ll quickly encounter complexities, like navigating different markets and working with various agencies, as seen in this helpful guide on navigating complexities international ppc working with agencies. Fortunately, implementing a referral program in WordPress can boost user engagement and expand your community, making it a valuable tool in your overall digital strategy.
The user is then logged in and directed to the dashboard.
Security and Validation
Protecting user data and preventing malicious activities are paramount when implementing user invitation features. Robust security measures, including validation techniques and proper account verification, are crucial to maintain a safe and reliable platform. This section delves into essential security best practices and mitigation strategies for user invitations.Implementing strong security measures prevents unauthorized access and maintains data integrity, ensuring a secure environment for all users.
Comprehensive validation ensures that only legitimate users are invited and registered, safeguarding the platform from spam and fraudulent activities.
Want to let users invite their friends to join your WordPress site? It’s a great way to grow your community! While figuring out that process, you might also need to adjust your site’s default text, like on a “Just Another WordPress Site.” Fortunately, there’s a straightforward way to modify that – check out this guide on how to easily change the just another WordPress site text.
Once you’ve got that handled, you can get back to making it easy for people to bring their friends into your WordPress community.
Security Best Practices for User Invitations
Thorough validation of user invitations safeguards against potential threats. Implementing strong password policies, regular security audits, and user account verification mechanisms are vital steps to protect the system from unauthorized access and malicious activity.
- Input Validation: Rigorous input validation is a fundamental security measure. All data received from user input, especially invitation codes or email addresses, must be thoroughly examined to ensure it conforms to expected formats and prevents injection attacks. For instance, carefully check email addresses for valid syntax to prevent malicious code from being embedded.
- Sanitization: Sanitizing user-supplied data is crucial to prevent cross-site scripting (XSS) attacks. All user inputs should be sanitized before being used in the application. This involves removing or encoding potentially harmful characters, ensuring that user-provided data does not compromise the security of the system.
- Regular Security Audits: Regular security audits are vital for identifying and addressing vulnerabilities. Security experts can conduct thorough assessments to pinpoint potential weaknesses in the system’s architecture, allowing for proactive mitigation strategies.
Potential Security Vulnerabilities and Mitigation Strategies
Identifying and addressing potential vulnerabilities is essential to maintain a secure platform. Vulnerabilities like SQL injection or cross-site scripting (XSS) can compromise user accounts and data integrity.
- SQL Injection: SQL injection attacks exploit vulnerabilities in the application’s database interaction logic. This occurs when user input is not properly sanitized before being used in SQL queries. To mitigate this risk, use parameterized queries, which isolate user input from the SQL command, preventing attackers from injecting malicious SQL code.
- Cross-Site Scripting (XSS): XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. This can occur when user-supplied data is not properly sanitized and displayed on the page. To prevent XSS, encode all user inputs before displaying them on web pages to neutralize the effect of malicious code.
- Brute-Force Attacks: Brute-force attacks attempt to guess user credentials repeatedly. Implement rate limiting and account lockout mechanisms to deter these attacks. These mechanisms limit the number of login attempts within a specific timeframe to mitigate brute-force attacks.
Data Validation Techniques
Data validation techniques are vital to ensure data integrity and prevent malicious input. These techniques help ensure that only valid data is processed, minimizing the risk of unexpected behavior and system crashes.
- Input Filtering: Filtering user inputs based on predefined rules ensures that only valid data is processed. Filtering can include checks for specific character sets, data types, and length restrictions. This helps prevent the introduction of harmful data into the system.
- Regular Expressions: Regular expressions are powerful tools for validating complex data patterns. They can be used to ensure that user input adheres to specific formats, such as email addresses or phone numbers. This helps prevent the introduction of incorrect or incomplete data.
- Data Type Validation: Validating the data type of user input is critical. Ensure that user-provided data conforms to the expected data types (e.g., integers, strings, dates). This prevents unexpected errors and potential security vulnerabilities.
Validating User Accounts
Validating user accounts is essential to prevent spam or fraudulent activities. Verification processes help ensure that the users being invited are legitimate and authorized to register.
- Email Confirmation: Implementing email confirmation for user accounts prevents unauthorized registrations and helps confirm the validity of user accounts. Send a confirmation email to the provided email address and request the user to click on a link to confirm their registration. This process ensures that the account belongs to a real user.
- Invitation Code Verification: Verification of invitation codes ensures that only invited users can register. The invitation code should be checked against a database to verify its validity before allowing the user to proceed with registration.
- User Role Verification: Verify the roles of users who are inviting others. Restrict the ability to invite users to those who hold the appropriate permissions, ensuring that only authorized individuals can invite new users.
Customization and Extensibility: How To Allow Users To Invite Their Friends To Register In WordPress
Beyond the core functionality of the friend invitation system, customization and extensibility are crucial for tailoring the experience to specific needs. This involves adapting the invitation process to incorporate branding elements, handling unique use cases, and enabling users to customize the look and feel of the invitation emails. This flexibility ensures the system remains adaptable as user requirements evolve.
Customizable Invitation Email Template
A customizable invitation email template empowers users to control the visual and textual aspects of the invitations. This allows for brand consistency and provides a more engaging user experience. The design should prioritize clarity, providing crucial information such as registration links and important instructions. An important consideration is email deliverability, ensuring that the invitation emails don’t end up in spam folders.
| Element | Customization Options |
|---|---|
| Subject Line | Allow modification of the subject line, potentially including user-specific information like the friend’s name. |
| Sender Name | Permit customization of the sender name to match the brand’s identity. |
| Body Text | Enable the inclusion of personalized messages, special offers, or unique branding elements. |
| Call to Action Button | Customize the button text and design to match the brand’s aesthetic. Ensure the button links to the appropriate registration page. |
| Footer | Allow for the addition of the company’s contact information and terms of service links. |
Adding Custom Fields to the Invitation System
Adding custom fields to the invitation system provides flexibility for gathering additional information from the inviting user. This allows the system to cater to specific use cases, such as collecting information about the reason for the invitation or a discount code for the invited user. Consider using validation to ensure the collected data is appropriate and reliable.
- Reason for Invitation: A text field to capture the reason why the user is inviting a friend. This could be a referral program, a group activity, or another specific circumstance.
- Discount Code: A field to include a discount code or special offer for the invited user, further incentivizing participation. This can be integrated with the user’s registration.
- Additional Notes: A text area where the inviting user can provide any additional instructions or comments to the invited user. This might be helpful for group projects or events.
Example of a Customized Invitation Email
This example demonstrates a customized invitation email. Note the personalization and branding elements incorporated into the design. The email uses a friendly tone and includes clear instructions on how to register.
“Subject: [User Name] Invited You to Join [Your Site Name]!”
Body:Hi [Invited User Name],[User Name] has invited you to join [Your Site Name]! We’re excited to have you.[Your Site Name] is a platform for [brief description of the site].Click this link to register: [Registration Link]Thank you,The [Your Site Name] Team[Website URL]
Error Handling and Feedback
A smooth user experience hinges on effectively handling errors and providing informative feedback. This section details strategies for managing potential issues during the friend invitation and registration process, ensuring a positive interaction for all users. Clear error messages and confirmation mechanisms are crucial for guiding users and preventing frustration.Robust error handling isn’t just about preventing crashes; it’s about providing a helpful experience for the user.
This involves anticipating potential problems, implementing preventative measures, and designing user-friendly feedback mechanisms to guide them towards a successful outcome.
Error Message Design
Providing clear and concise error messages is vital for user comprehension and effective troubleshooting. A well-structured error message should communicate the issue, its potential cause, and steps the user can take to resolve it.
- Specificity is Key: Instead of a generic “Error,” tailor messages to the specific problem. For example, “The email address you entered is invalid” is more helpful than simply “Error.”
- Contextual Information: Include relevant contextual information in error messages. If the user is trying to invite a friend, mention that. For example, “The email address ‘[email protected]’ is invalid. Please try again.”
- Actionable Steps: Guide the user toward a solution. Suggest how to correct the error. For instance, “To proceed, please enter a valid email address.”
- Avoid Technical Jargon: Use language that the average user can understand. Avoid technical terms or cryptic error codes.
Handling Invalid Email Addresses
Validating email addresses is essential to prevent issues during the invitation process. Incorrect or malformed email addresses can lead to failed invitations or registration attempts.
- Validation Rules: Implement strict validation rules for email addresses. Use a robust regular expression to ensure the format is correct.
- User Feedback: Display clear error messages when the email format is incorrect. For instance, “Please enter a valid email address in the format ‘[email protected]’.”
- Preventing Duplicate Invitations: Check if the invited email address already exists in the database. If it does, provide a message indicating that the user has already been invited or is registered.
Handling Non-Existent Users
The system should gracefully handle cases where the invited user doesn’t exist.
- Verification Mechanism: Ensure the invited user exists in your system before proceeding with the invitation. Implement a check to verify that the email address belongs to an active user account.
- Informative Feedback: If the user doesn’t exist, provide a clear message, such as, “The user with the email ‘[email protected]’ does not exist. Please ensure the email address is correct or invite them directly.”
Successful Invitation and Registration Feedback
Confirming successful invitations and registrations is just as important as handling errors. Positive feedback reinforces user actions and motivates them to continue using the system.
- Confirmation Messages: Provide clear messages confirming that the invitation has been sent. For example, “The invitation to ‘[email protected]’ has been sent successfully.”
- Registration Confirmation: When a user registers after an invitation, provide a confirmation email and/or message on the invitation page. This reinforces the action and completes the process.
- Automated Emails: Use automated emails for confirmations and to provide further information.
Example Error Messages
| Scenario | Error Message |
|---|---|
| Invalid Email Format | “Please enter a valid email address in the format ‘[email protected]’.” |
| User Already Exists | “The user ‘[email protected]’ is already registered or invited. Please try inviting a different user.” |
| Non-existent User | “The user with the email ‘[email protected]’ does not exist. Please ensure the email address is correct or invite them directly.” |
| Invitation Failed | “An error occurred while sending the invitation. Please try again later.” |
End of Discussion
In conclusion, enabling user-to-user invitations in WordPress can significantly enhance your website’s community engagement. By carefully considering the invitation mechanisms, plugin integration, database design, and user experience, you can build a robust and secure system. Remember to prioritize security, error handling, and user experience to ensure a positive and effective invitation flow for your users. This detailed guide provides a comprehensive blueprint to get started.